Using ssh-agent with KeePassXC
Table of Contents
If you’re here, I assume you know what SSH keys are, and that you should use a passphrase for the private key. I’ll also assume you’ve heard of KeePass, the defacto locally run password manager.
I try to use SSH keys to log into all of my various Linux servers. Traditionally, I’ve created the keys without passphrases, knowing it’s a bad practice. But who has time to look up the passphrase every time they want to connect to a server? Yes, many SSH apps have the option to store them, but I always imagined those apps storing them in some totally insecure way. Kind of like when you use your web browser as a password manager. When I switched to Arch & Plasma on my home rig, I started using ssh-agent with KWallet. I didn’t like how that worked in terms of workflow, and it also didn’t seem as secure as I wanted. But it did the job.
I had been using KeePass on Windows for the last decade+. When I moved to Arch, I was reloading all the things, and looked into a more Linux-native KeePass option. I found KeePassXC, and WOW, so awesome compared to KeePass. Why the hell wasn’t I using this the whole time? In looking at the FAQ on their site, I saw a mention of ssh-agent support and kept that in the back of my mind. I recently reinstalled Arch on my box and figured I should see how the ssh-agent integration worked. It’s awesome! Enough so that I wanted to write a quick post in the hopes it inspires someone else to make the jump. Or at least serves as a friendly reminder to not be like me for so long and roll with SSH keys without a passphrase haha 😛
Enabling ssh-agent #
Most guides suggest putting the below snippet into your .bashrc, which works and is what I’ve done in the past.
if ! pgrep -u "$USER" ssh-agent > /dev/null; then
ssh-agent -t 1h > "$XDG_RUNTIME_DIR/ssh-agent.env"
fi
if [ ! -f "$SSH_AUTH_SOCK" ]; then
source "$XDG_RUNTIME_DIR/ssh-agent.env" >/dev/null
fi
However, in reading the Arch Wiki again on this, I noticed the (arguably small) entry “Start ssh-agent with systemd user”. Since Arch is all about using systemd, I’ve also been trying to use it for all the things.
Enable ssh-agent for current user using systemd:
systemctl --user enable --now ssh-agent
Along with that, you still need to have the SSH_AUTH_SOCK env var set so any apps looking for it will know to use ssh-agent:
Edit ~/.bashrc, append:
#ssh-agent.service
export SSH_AUTH_SOCK=$XDG_RUNTIME_DIR/ssh-agent.socket
The Konsole env is now set up to use ssh-agent, but you need to also set SSH_AUTH_SOCK in Plasma, as it uses it’s own Environment Variables.
cat << EOF > ~/.config/plasma-workspace/env/ssh-agent-env.sh
#!/bin/bash
export SSH_AUTH_SOCK=\$XDG_RUNTIME_DIR/ssh-agent.socket
EOF
Now the ssh-agent is running, and will launch next time you log into a Plasma Session. Both the Konsole and Plasma environments now have the needed env var.
SSH Keys in KeePassXC #
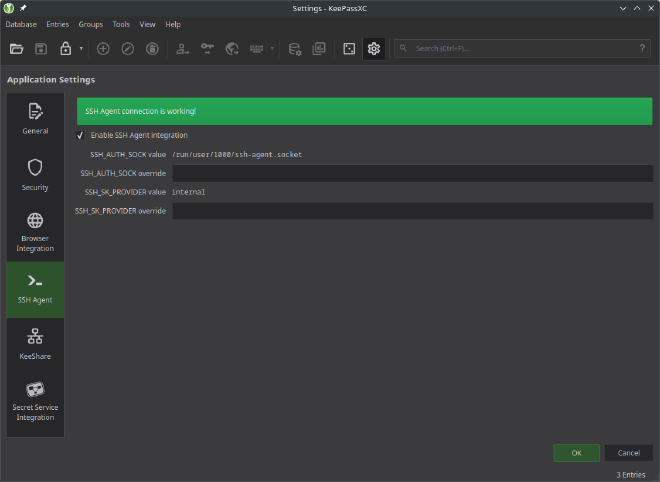
Launch KeePassXC, go to Tools -> SSH Agent, check the box and make sure KeePassXC can connect to the ssh-agent socket.
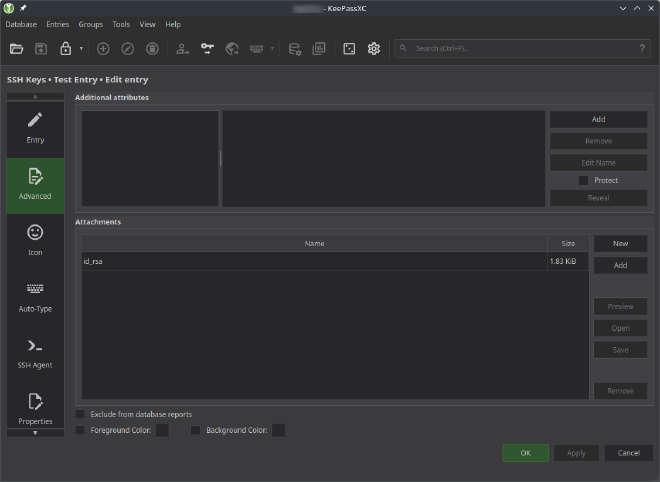
Create an Entry in KeePassXC, setting the SSH Private Key Passphrase as the Password for the Entry. On that Entry, add the SSH Private Key under the Advanced tab:
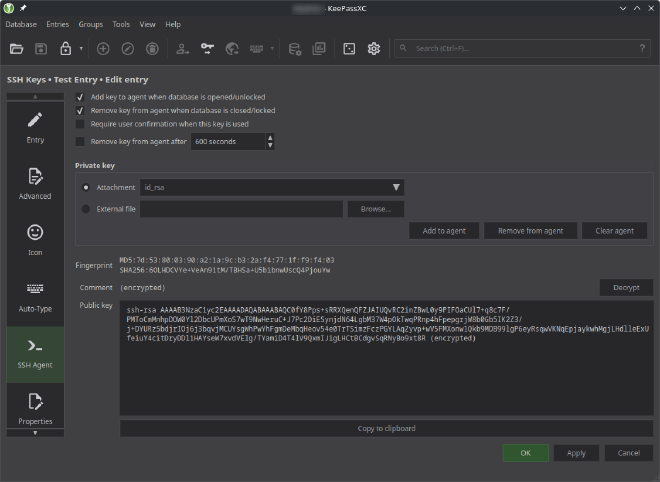
On the SSH Agent tab, select the Attachment as the Private Key. I also like to select the options to Add & Remove the keys from ssh-agent when KeePassXC is opened & closed.
Conclusion #
That’s it! I’ve loaded all of my private key files and passphrases into KeePassXC, and when the database is open and unlocked, I can ssh into hosts with ease. I love this approach for a few reasons:
- I have to explicitly unlock the KeePassXC database to have the keys available.
- I can delete all my private key files, as they’re inside the KeePassXC database now.